
While many of us probably don’t think much of our demise (or incapacitation) , inevitably it will happen, what’s worse particularly for our loved ones is when it happens unexpectedly , and with so much of our modern life lived online , there’s often a bunch of accounts and files the hold important financial , legal and personal records that may become inaccessible (or at a minimum a lot of bureaucratic red tape) should we have an untimely demise.. so its important for your loved ones to have an easy an convenient file (aka “death file”) . The focus of this post is on the digital file itself, but there’s a lot more to end of life planning checklist than just one file, you can read more about it here.
A Sample Digital Death File
To get an idea of what a digital death/afterlife file looks like , I have linked a Google Docs template file, (copy this blank document to your account)
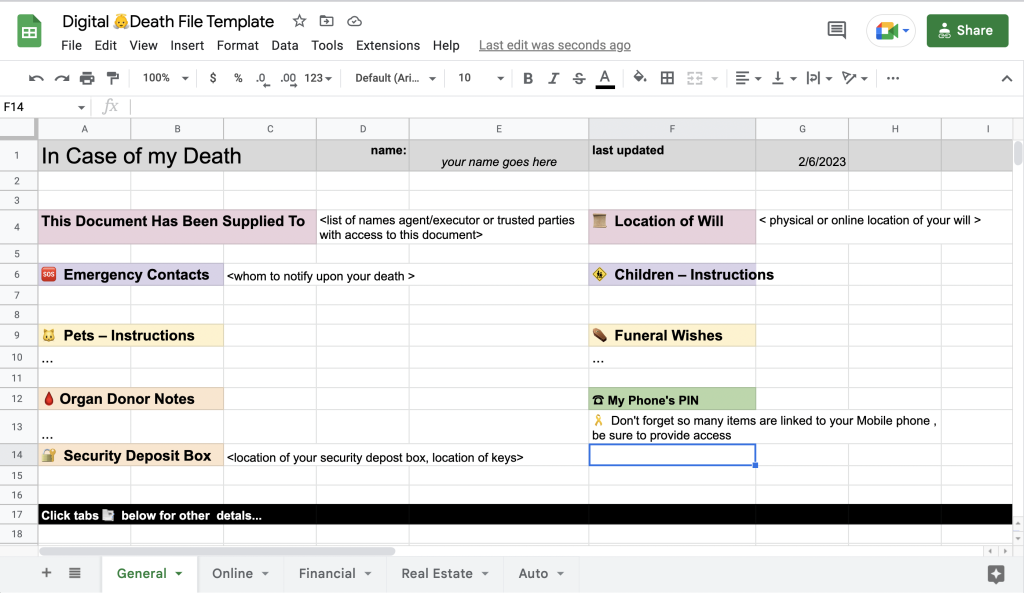
There are many possible templates, but at its most basic, it’s a simple spreadsheet/word file, with tabs /sections (see below) that cover the various important parts of a your online accounts, financial documents, and other import assets. It should contain information and instructions for accessing, managing, and distributing your online accounts, assets, and personal data after you pass away.
ProTip: Be sure to leave your mobile ? phone’s PIN or access credentials as many services use your phone for 2FA.
? Reminder
Some suggested items to include in a digital death file are:
- A list of all your online accounts (e.g. social media, email, banking, etc.).
- Usernames and passwords for each of your online accounts.
- Information on any online assets, such as domain names, online storage, and websites.
- Details on any digital currencies you own and how to access them.
- Instructions on what to do with your digital assets (e.g. transfer ownership, close accounts, etc.).
- Designated trusted individuals or executors who will be responsible for managing your digital death file and carrying out your wishes.
- Any relevant legal documents or agreements related to your digital assets.
- Location of important documents,
- Deed to a home(s)
- Last will and Testament
- Titles to automobile, motorcycles, boats, planes and other motorized vehicles
- Location of safety deposit boxes, storage facilities
Giving Access to this sensitive data
The next question after you have created your digital archive, is how can I securely and conveniently provide access to it. Obviously it goes without say that only trusted family or friends (trusted parties) should be the ones that have access to this file. The first and most obvious way is to place this file in a secure online cloud provider (Google Docs, Microsoft Cloud ) and secure it , then share it securely with specific folks.
Finally for digital files, an alternate approach is to encryprt the file with a password , the provide the password protected file to all the relevant trusted parties , and give them the key through a separate channel, like an sms text message . Doing this puts the file securely encrypted into their possession so they won’t have to be searching for it.
There may also be case where you don’t want to just trust one person to open the file (prematurely) or only have the file be open when multiple people agree and have a legitimate need to open it (you’ve passed or are incapacitated) . In this case the easiest approach is to create a very long password, and give separate segments of the password to different people. The only issue with this separate password segments approach is if one of the multiple parties, is unreachable, then the password file may be locked, so a backup of the complete password and should be stored in an alternate trusted location.
If you don’t offer your trusted parties the access credentials, they still may be able to access your digital file (upon your passing) , but will then need to follow a more formal procedure from the various cloud providers on how to access a deceased persons file.
The next alternative if you don’t feel comfortable with the file online is keep it offline, such as in a USB or even in a printed form, that is clearly marked , then and store it in a safety deposit box or other secure location, and importantly share that location (and access information) with your trusted parties.
Finally don’t forget ? , please sure to update this file periodically, once or twice a year.
State Laws and Rights
This post is mostly about access to your accounts, and providing a simple and convenient way for trusted parties to get to those accounts. But keep in mind ultimately access and ability to move /control those assets is determined ( In the United States), by inheritance laws that vary by state, but there are some general principles that apply across the country. These laws will apply to getting all the requisite records necessary.
If a person dies without a will (intestate), the laws of the state in which they resided will determine who inherits their property. Typically, spouses and children are first in line to inherit, followed by other family members such as parents or siblings. If a person has no living relatives, their property will typically go to the state.
If a person dies with a will (testate), the terms of the will dictate who inherits their property. The will must be properly executed and meet the requirements of the state in which the deceased person resided. If the will is found to be invalid, the laws of intestacy will apply.
In some states, a surviving spouse may have the right to a certain portion of the deceased person’s estate, even if the will says otherwise.
It’s important to keep these ideas in mind, since digital records, and the accounts or property they give you access to are ultimately bound by the inheritance laws of your sate.
One popular method is called Shamir’s Secret Sharing. Here’s how it works:
Choose a threshold (t) of people required to reconstruct the secret key. For example, if you have 5 people and you want at least 3 of them to collaborate to open the document, set t=3.
Use Shamir’s Secret Sharing algorithm to split the secret key into multiple shares. Each person will receive one share.
Distribute the shares among the people. Make sure each person receives only one share.
To open the document, at least t people (in our example, 3 people) must collaborate and combine their shares to reconstruct the secret key.
Once the secret key is reconstructed, it can be used to decrypt and open the document.
This method ensures that no single person can open the document, as they would need the collaboration of at least t-1 other people to reconstruct the secret key. It provides a secure way to share sensitive information among multiple parties while maintaining control over access.